Call a Specialist Today! 844-294-0778
PA-Series
Compare firewall specifications
PA-Series firewalls span branch offices to hyperscale data centers. Compare key performance metrics across every hardware platform to identify the right model for each network segment.
Contact a specialist View all modelsCompare specifications across platforms
All throughput values represent real-world application-mix traffic. Session capacity and connection rates are measured under standard test conditions with security services enabled.
Select a deployment category below to compare models within each tier. Individual model pages contain full port layouts, power specifications, and licensing details.

Branch and retail
PA-400 and PA-500 series models deliver 1.2 to 8.5 Gbps firewall throughput with Precision AI and optional 5G connectivity.

Campus and gateway
PA-1400 and PA-3400 series models deliver 8.5 to 35 Gbps firewall throughput with multi-gig ports and fiber connectivity.
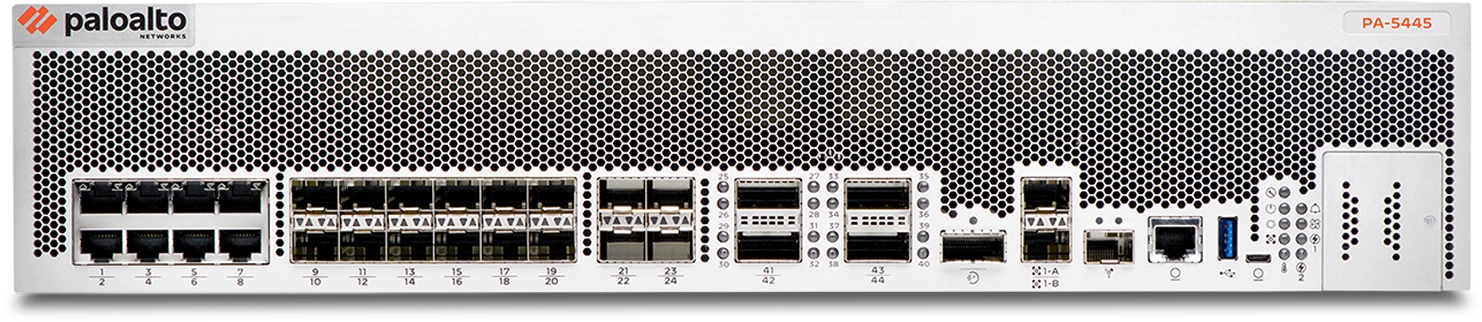
Data center
PA-5400, PA-5500, and PA-7500 series platforms scale from 52 Gbps to 1.5 Tbps firewall throughput for hyperscale environments.
Performance specifications by deployment tier
Select a category to compare throughput, session capacity, and connection rates across models within each deployment tier.
Precision AI-powered branch security with fanless designs, optional 5G, and PoE+ support.
PA-400 series
| Model | Firewall throughput | Threat prevention throughput | Max sessions | New sessions/sec |
|---|---|---|---|---|
| PA-410 | 1.4 Gbps | 0.8 Gbps | 64,000 | 11,000 |
| PA-415 | 1.5 Gbps | 0.8 Gbps | 64,000 | 11,000 |
| PA-440 Popular | 2.6 Gbps | 1.25 Gbps | 198,976 | 34,000 |
| PA-445 | 2.7 Gbps | 1.2 Gbps | 198,976 | 34,000 |
| PA-450 | 3.3 Gbps | 2.1 Gbps | 300,000 | 48,000 |
| PA-455 | 3.6 Gbps | 2.3 Gbps | 300,000 | 56,000 |
| PA-460 | 4.6 Gbps | 3.0 Gbps | 400,000 | 67,000 |
PA-500 series
| Model | Firewall throughput | Threat prevention throughput | Max sessions | New sessions/sec |
|---|---|---|---|---|
| PA-505 | 1.2 Gbps | 0.8 Gbps | 64,000 | 10,000 |
| PA-510 | 1.8 Gbps | 1.2 Gbps | 98,000 | 15,000 |
| PA-520 | 2.8 Gbps | 1.8 Gbps | 148,892 | 25,000 |
| PA-540 | 3.8 Gbps | 2.2 Gbps | 298,849 | 50,000 |
| PA-550 | 6.5 Gbps | 4.5 Gbps | 448,832 | 70,000 |
| PA-560 | 8.5 Gbps | 6 Gbps | 598,624 | 100,000 |
High-speed enterprise edge platforms with multi-gig ports, fiber connectivity, and rack-mount form factors.
PA-1400 series
| Model | Firewall throughput | Threat prevention throughput | Max sessions | New sessions/sec |
|---|---|---|---|---|
| PA-1410 Recommended | 8.5 Gbps | 4.5 Gbps | 945,000 | 100,000 |
| PA-1420 | 9.5 Gbps | 6.2 Gbps | 1,398,646 | 140,000 |
PA-3400 series
Hyperscale and quantum-ready platforms with massive throughput, 100G/400G ports, and tens of millions of concurrent sessions.
PA-5400 series
| Model | Firewall throughput | Threat prevention throughput | Max sessions | New sessions/sec |
|---|---|---|---|---|
| PA-5410 | 52 Gbps | 35.0 Gbps | 4,990,000 | 270,000 |
| PA-5420 | 70 Gbps | 50.0 Gbps | 6,990,000 | 370,000 |
| PA-5430 | 82 Gbps | 60 Gbps | 8,990,000 | 380,000 |
| PA-5440 | 90 Gbps | 70 Gbps | 23,990,000 | 390,000 |
| PA-5445 New | 90 Gbps | 76 Gbps | 47,990,000 | 449,000 |
PA-5500 series
| Model | Firewall throughput | Threat prevention throughput | Max sessions | New sessions/sec |
|---|---|---|---|---|
| PA-5540 | 97 Gbps | 67 Gbps | 30,000,000 | 466,000 |
| PA-5550 | 127 Gbps | 82 Gbps | 30,000,000 | 550,000 |
| PA-5560 | 200 Gbps | 105 Gbps | 60,000,000 | 700,000 |
| PA-5570 | 275 Gbps | 143 Gbps | 60,000,000 | 900,000 |
| PA-5580 | 380 Gbps | 194 Gbps | 120,000,000 | 1,200,000 |
PA-7500 series
| Model | Firewall throughput | Threat prevention throughput | Max sessions | New sessions/sec |
|---|---|---|---|---|
| PA-7500 | 1.5 Tbps | 1.44 Tbps | 440,000,000 | 7,200,000 |
Ruggedized OT and IoT platforms
Industrial-grade appliances certified for extreme temperatures, vibration, and electromagnetic interference. Same PAN-OS security capabilities in hardened form factors.
| Model | Firewall throughput | Threat prevention throughput | Max sessions | New sessions/sec |
|---|---|---|---|---|
| PA-410R | 1.4 Gbps | 0.78 Gbps | 65,536 | 11,400 |
| PA-410R-5G | 1.4 Gbps | 0.78 Gbps | 65,536 | 11,400 |
| PA-450R | 3.2 Gbps | 1.4 Gbps | 198,976 | 48,000 |
| PA-450R-5G | 3.2 Gbps | 1.4 Gbps | 198,976 | 48,000 |
| PA-455R-5G | 3.2 Gbps | 1.8 Gbps | 198,766 | 48,000 |
Consistent security across all platforms
Every PA-Series firewall runs PAN-OS and shares the same security architecture, policy framework, and management interface regardless of form factor or throughput tier.
Single-pass architecture
Traffic is inspected once for all security functions including App-ID, User-ID, Content-ID, and decryption. This eliminates the latency of serial processing across multiple engines.
Cloud-delivered security services
Advanced Threat Prevention, Advanced WildFire, DNS Security, and Advanced URL Filtering are delivered from the cloud and apply consistently across all PA-Series models.
Centralized management
Panorama provides unified policy management, logging, and reporting across all firewalls. Strata Cloud Manager extends visibility with AIOps-driven insights.
Zero Trust network security
App-ID, User-ID, and Device-ID enable least-privilege access policies. Every flow is classified and controlled regardless of port, protocol, or encryption.
Get help selecting the right model
Network security specialists can assist with platform sizing, licensing options, and competitive pricing for PA-Series firewalls.
