Unit 42: Managed Detection and Response (MDR)
With our team of security experts, we’ll detect and respond to cyberattacks whenever they occur. By bringing us in, your team can scale and focus on what matters most. Our analysts have extensive experience in quickly identifying and stopping the malicious activity most likely to impact your organization.
Download the datasheet
Best-in-Class Extended Detection and Response and
Unit 42 Security Expertise, Delivered as a Managed Service
A Service Delivered by Palo Alto Networks World-Renowned Unit 42
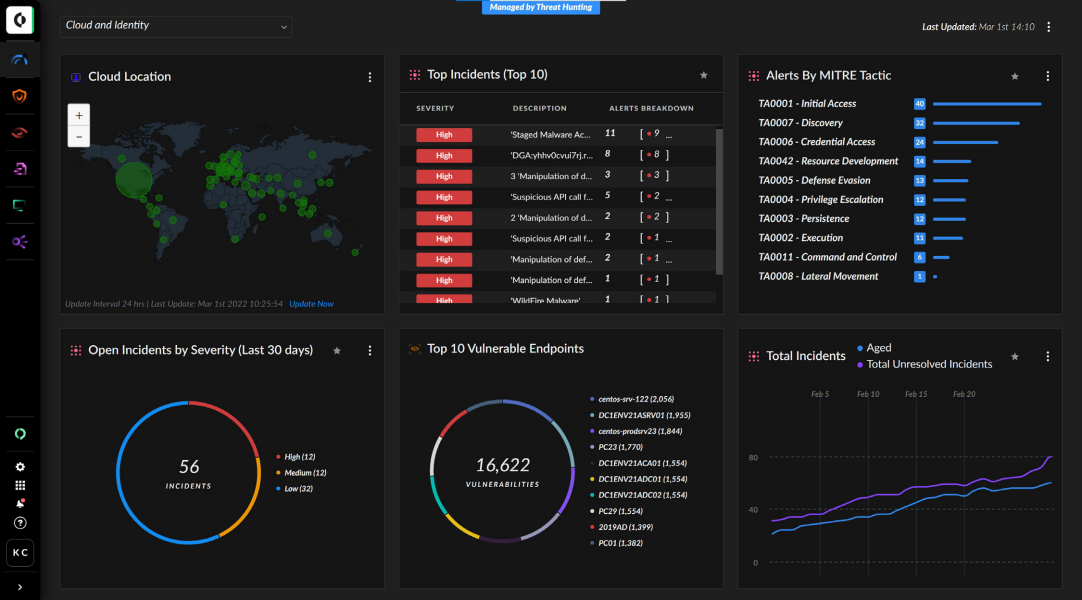
Unit 42 experts work for you to detect and respond to cyberattacks 24/7, allowing your team to scale fast and focus on what matters most. We use Cortex XDR, so our analysts have unmatched visibility into all data sources (endpoint, network, cloud, and identity) to quickly identify and stop malicious activity most likely to impact your organization:
- Built on Cortex XDR
- Backed by Unit 42 expertise
- Enriched with world-class threat intelligence
Let Unit 42 MDR Address These Challenges
- Cyberattacks are increasing in speed and sophistication. The threat landscape is shifting to advanced, multistep attacks. Without constant coverage, proactive hunting, and immediate response, you may not stop these attacks before it’s too late.
- Prioritizing limited resources to combat the changing threat landscape. Threat actors and their tactics change daily, and many organizations lack broad visibility to interpret and recognize attack indicators.
- Security teams need help managing an endless backlog of alerts. Overwhelmed by too many lowfidelity alerts, many security teams don’t have additional time for threat hunting.
Benefits
Our experience is your experience
We’ll apply our years of experience protecting businesses, governments and countries to monitor your environment and look for anything suspicious. Our analysts work 24/7, sorting through Cortex XDR® data to bring the full picture together. With this knowledge, our team can accurately detect attacks and understand their nature.
Built on industry-leading XDR technology
Cortex XDR automatically collects data across endpoint, network and cloud. This data is a critical advantage, establishing the insight and context needed to detect and respond to attacks on your organization.
Backed by Unit 42 expertise
With more than 200 analysts, researchers and engineers, Unit 42 is trusted by CISOs globally. By adding this expertise to your team, you elevate your capabilities, establishing greater confidence and reducing the need to hire hard-to-find experts.
Enriched with world-class threat intelligence
Unit 42 analysts take advantage of extensive telemetry and threat intel from over 10 years of malware analysis experience, as well as 30M+ new samples and 500B events received each day. This means our incident response efforts have an unmatched breadth and depth of data to work with.
Watch how Unit 42 MDR supercharges your defenses
With the Unit 42 Managed Detection and Response service, Unit 42 experts work for you to detect and respond to cyberattacks 24/7, so your team can focus on what matters most. Unit 42 analysts will respond to incidents, perform full investigation, containment and remediation of threats within your Cortex XDR environment.
Service Features
Here’s what we deliver
Unit 42 experts work for you 24/7 to detect and respond to attacks, allowing your team to scale fast and focus on what matters most.

Continuous Monitoring
Our security experts will monitor your Cortex XDR environment for alerts, events and indicators 24/7/365.
- Comprehensive visibility: Cover endpoints, network, cloud, and identity data with SLO-driven, 24/7 monitoring and analysis of security incidents identified in Cortex XDR.
- Alert management and incident triage: Automated and manual review to analyze alert details, incidents, and generate BIoC or IoC rules to understand context and follow-up actions
- Notification and security event escalation: Escalation of incidents that require attention, leveraging built-in logic and alert stitching aligned with MITRE ATTACK framework.
Proactive Threat Hunting
As new vulnerabilities are identified or a new threat actor is in the news, our threat hunters will proactively look for indicators of attack or vulnerable systems that have not been patched, providing detailed impact reports and recommended actions.
- 24/7 hunting for advanced threats: Sophisticated threat hunting based on analysis of suspicious signals, Cortex XDR analytics, custom detection rules, and Unit 42 research to identify and stop new threats.
- High-fidelity threat intel: Integration of industry-leading, comprehensive Unit 42 threat intelligence based on telemetry and detections from Palo Alto Networks products across our global customer base to inform and enrich investigations
- Actionable reporting: Threat reports detailing the scope, source, and attack tools of threats, along with recommended actions; impact of emerging threats affecting multiple organizations to stay ahead of high-profile cyberattacks.
- Direct assistance: Easy access to threat hunting team to ask questions and get guidance about threats.

Investigation & Response
Should the need arise, Unit 42 analysts will immediately begin investigating and containing the event, keeping in close communication with your team.
- Contain threats quickly: Analysts will quickly contain active threats by isolating endpoints and removing malicious files or processes using Cortex XDR
- Streamlined investigations: Investigate endpoints, analyze forensic artifacts, and network and cloud telemetry to identify incident root cause and scope.
- Recover rapidly: Use of Cortex XDR to remove malicious files, registry keys, and restore damaged files

Impact & Threat Reports
Based on threats found by Unit 42 – in your environment or in the wild – we will automatically create a report with the details of what we have discovered. If threats are found in your environment, the Unit 42 team will open an incident in Cortex XDR and continue to issue reports with any new information.
- Health checks: Identify gaps in hardening requirements with endpoint security profiles, device control, host firewall, and disk encryption.
- Vulnerability assessments: Identify and quantify security vulnerabilities (CVEs) for applications installed on your endpoints.
- Host inventory: Review the inventory of hosts to quickly identify any IT or security issues.