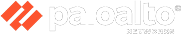
AI Security Posture Management (AI-SPM)
Gain visibility and control over models, GenAI and the AI supply chain. Stop new attack vectors before they materialize.
Download the datasheet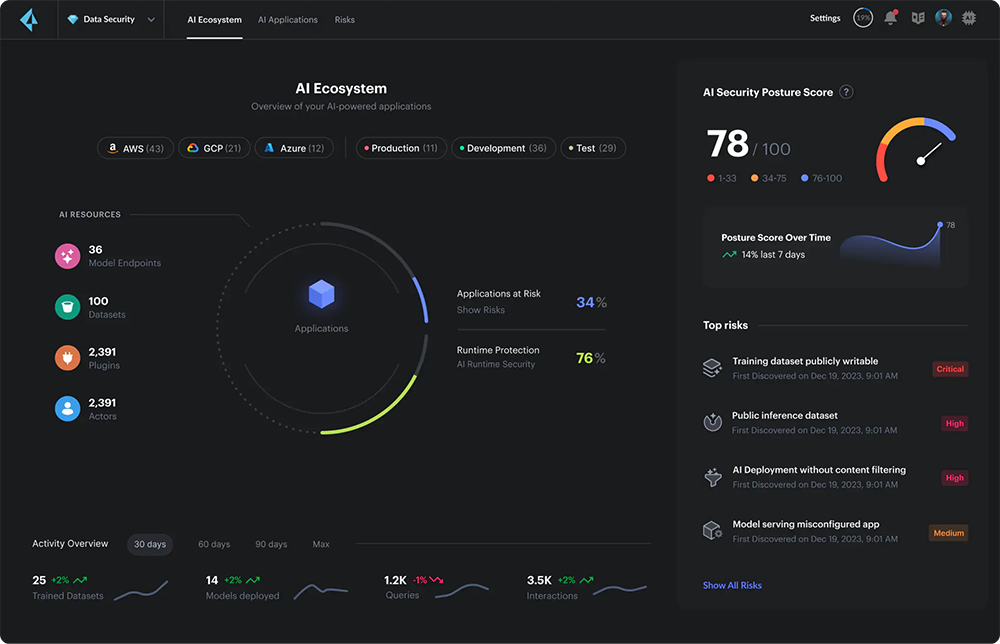
Why It Matters
The rapid adoption of AI/ML leads to model corruption, AI model misuse and unwanted data exposure.
New AI attack vectors
Implementing new pipelines and infrastructure together with lack of unified visibility make organizations susceptible to new attacks.
Dealing with model sprawl issues
Lack of AI inventory can lead to shadow AI models, compliance violations and data exfiltration through AI-powered applications.
Governance is lacking
New AI-focused legislation mandates strict controls around AI usage and customer data that is fed into AI powered applications.

Datasheet: Securing the AI Landscape
High-Level Benefits
Protect and control AI infrastructure, usage and data
Maximize the transformative benefits of AI and large language models (LLMs) without putting your organization at risk. Prisma Cloud AI Security Posture Management (AI-SPM) gives you visibility and control over the three critical components of your AI security — the data you use for training or inference, the integrity of your AI models and access to your deployed models.
- Detect unsafe or unauthorized model usage.
- Reduce risk of data exposure from AI systems.
- Ensure compliance with current and upcoming regulations.
Our Approach to AI Security
The Prisma Cloud Solution
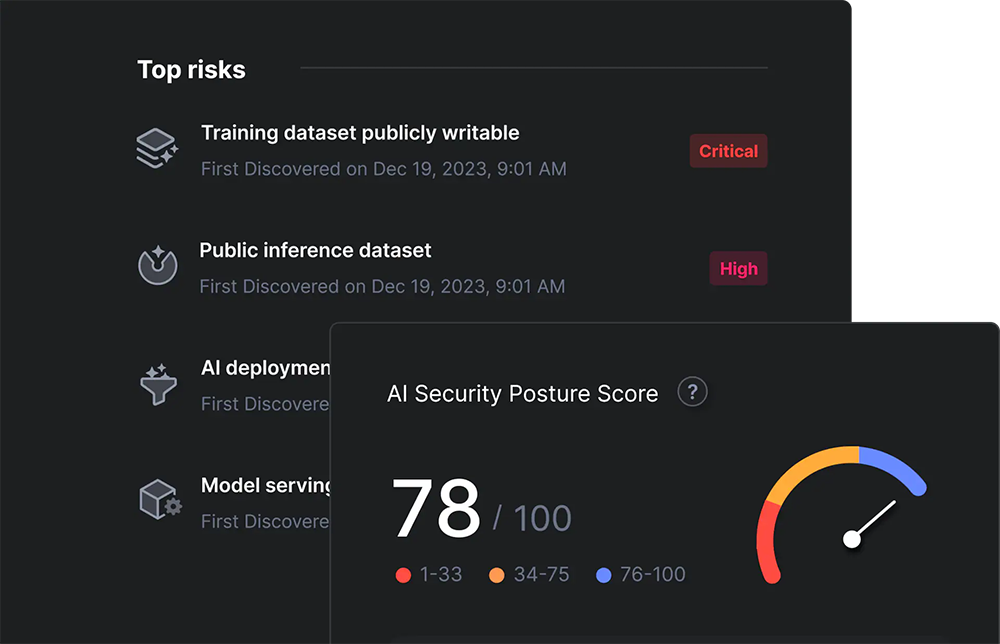
Visibility into AI Application Ecosystem
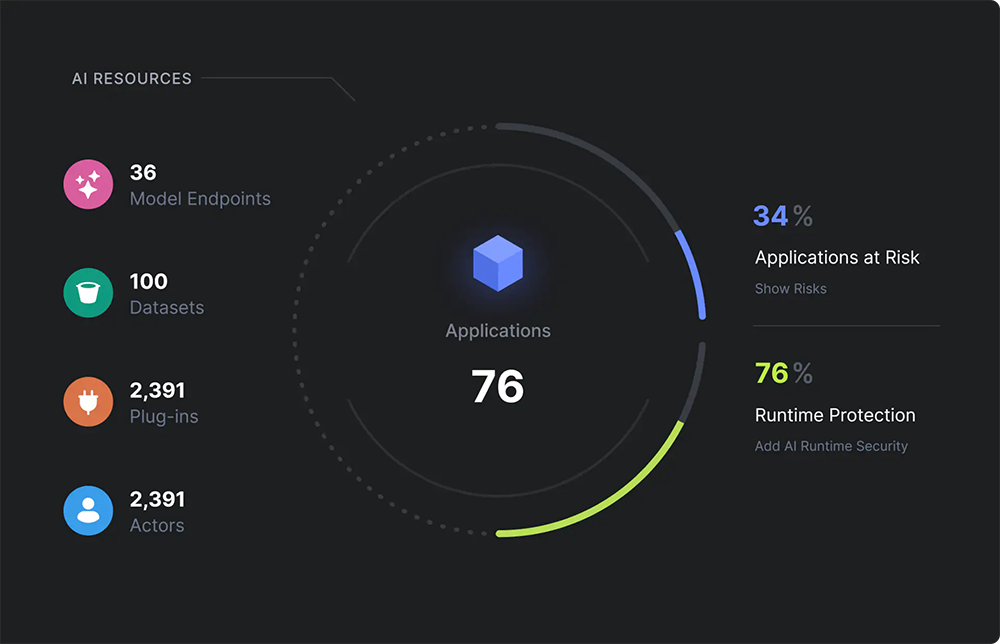
Discover all AI applications, models and associated resources. Identify and trace lineage of AI components used in applications.
AI App stack discovery
Discover all AI applications, models and associated resources.
AI lineage
Identify and trace lineage of AI components and data sources used in applications.
Model inventory
Catalog AI models deployed and identify updates.
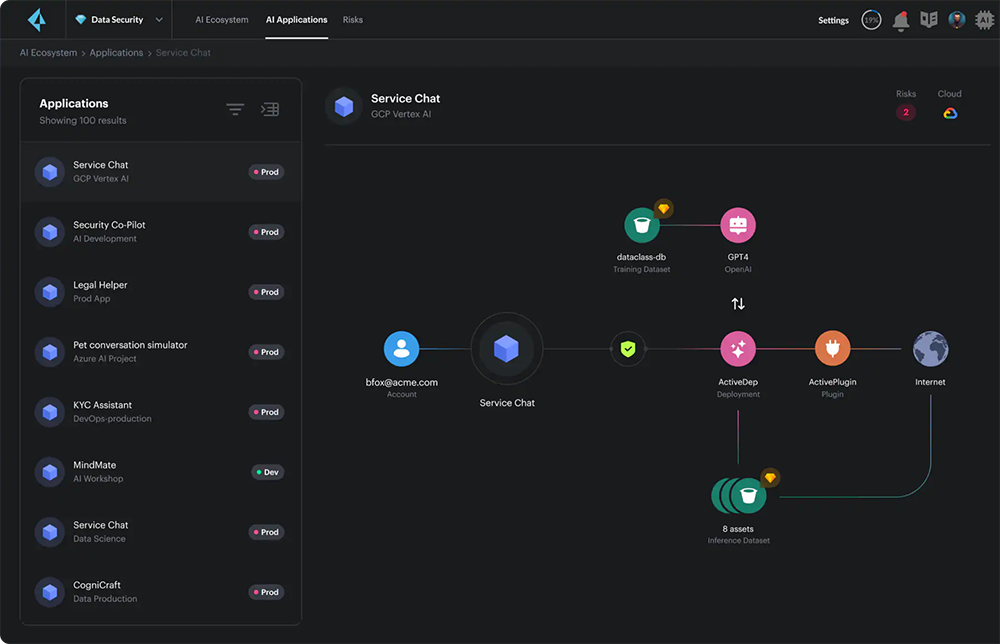
AI Model Risk Analysis
Identify vulnerabilities in the AI supply chain, and find misconfigured models and related cloud resources that can lead to manipulation, misuse and theft.
Prevent model compromise and theft
By identifying risks of adversaries to create a functional equivalent.
Find misconfigurations
By reducing overprivileged compute instances and models.
Avoid insecure plug-in design
By identifying overprivileged and vulnerable agents/workloads.
Trusted by innovators worldwide
Read how these customers keep their data safer with Prisma Cloud




