Managing network security can be a difficult task. Keeping up with the latest threats, monitoring the next hacking trend and dealing with adds, moves and changes can make for a very busy day. Inconsistent security device management mechanisms only make the administrator’s life more difficult.
Keeping ease of use and consistency as key development goals, the web interfaces for both Panorama and the individual platforms have the same look and feel, thereby minimizing the learning curve often associated with switching from single-device management to centralized management of multiple next generation firewalls. The Palo Alto Networks management tools make security policy management a straightforward process, using visualization tools, common application names and standard security terminology.
Application Command Center:
Application Command Center (ACC), is a powerful visualization tool that summarizes current network activity in a straightforward, easy to understand manner. An integral component of both Panorama and the device web-interface, ACC presents administrators with a visual summary of application, web, URL, threat and data transfer activity displayed in a straightforward, easy to understand manner. ACC can be modified in the following ways:
- Application usage: View top applications traversing the network by risk, by category or subcategory, by technology or by network risk profile.
- Web activity: View top URLs visited and blocked or top URL categories visited or blocked.
- Data filtering: Gain insight into the files and data patterns that are being sent across the network.
- Threat activity: View spyware, application vulnerability exploits, viruses and other malware that may be traversing the network.
App-Scope:
Whereas Application Command Center (ACC) gives an administrator a view into current network activity, App-Scope is a set of visualization tools that provides a comparative view of application activity (now vs a past timeframe). A standard feature of both Panorama and the device web-interface, App-Scope helps reduce the amount of time an administrator needs to investigate unusual behavior by answering some very common questions:
- How has application usage and user activity changed on the network?
- Which users and apps are consuming the most bandwidth?
- Which threats are consistently on the network?
- Where is traffic and threats coming from and going to?
Policy Management:
The increased visibility into network activity generated by App-ID, User-ID and Content-ID can help simplify the task of determining which applications are traversing the network, who is using them, the potential security risk and then easily determine the appropriate response. Armed with these data points, administrators can apply policies with a range of responses that are more fine-grained than allow or deny. Policy control responses include:
| Allow or deny |
Allow but scan |
| Allow based on schedule |
Decrypt and inspect |
| Apply traffic shaping |
Allow for certain users or groups |
| Allow certain application functions |
Any combination |
Using a policy editor that carries a familiar look and feel, experienced firewall administrators can quickly create flexible firewall policies such as:
- Assign Saleforce.com and Oracle to the sales and marketing groups by leveraging Active Directory integration.
- Enable only the IT group to use a fixed set of management applications such as SSH, telnet and RDP.
- Block bad applications such as P2P file sharing, circumventors and external proxies.
- Define and enforce a corporate policy that allows and inspects specific webmail and instant messaging usage.
- Control the file transfer functionality within an individual application, allowing application use yet preventing file transfer.
- Identify the transfer of sensitive information such as credit card numbers or social security numbers, either in text or file format.
- Deploy multi-level URL filtering policies that block access to obvious non-work related sites, monitor questionable sites and “coach” access to others.
- Implement QoS policies to allow media and other bandwidth intensive applications but limit their impact on business critical applications.
With a Palo Alto Networks next-generation firewall in place, customers can deploy positive enforcement model policies to block bad applications, protect the business applications and promote the secure use of end-user applications resulting in a more positive employee environment.
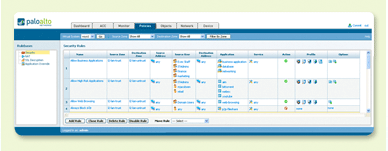
A familiar look and feel takes full advantage of existing firewall policy editing
skills, accelerating the deployment of application usage control policies.
|
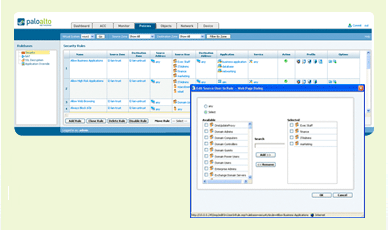
Transparent integration with Microsoft Active Directory facilitates policy creation based upon actual user and group information, in addition to traditional IP address methodologies. |
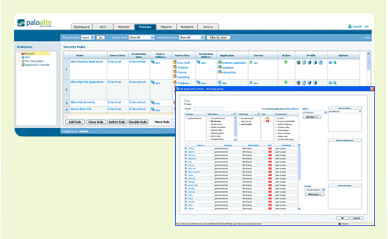
Selecting an application is done via the application browser which enables dynamic filtering on application category, subcategory, technology and behavioral characteristic. |
Application Browser:
The identity of the application is one of several pieces of the application visibility and control puzzle. The remaining pieces required to make a business decision on how to treat the application include more data on what the application is, its risk characteristics, and what technology it uses.
To enable an informed decision on how to treat an application, Palo Alto Networks presents additional background on every application identified in an application browser, providing fingertip access to a wealth of information. The application browser is a powerful research tool, accessible via the Palo Alto Networks website and as an integral piece of the policy management interface.
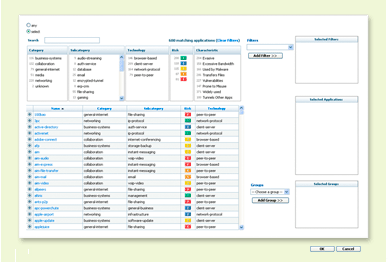
Application browser enables dynamic application filtering based
on category, subcategory, technology, risk and characteristic.
In either case, administrators can dynamically filter applications based on category, subcategory, underlying technology, and characteristic – including their file transfer capabilities, known vulnerabilities, ability to evade detection, propensity to consume bandwidth, and malware transmission/propagation. Additional application details include a description of the application, the commonly used ports and a summary of the individual application characteristics. Using the application browser, administrators can quickly research an application and immediately translate the results into a security policy.
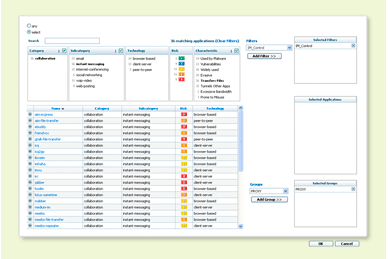
Filter results can be immediately translated into security policies.
In this example, a policy can be created that would allow or deny
use of all IM applications that can transfer files.
Reporting and Logging:
Using either Panorama or the individual device management interface, administrators have fingertip access to powerful reporting and logging to investigate and analyze security incidents, application usage and traffic patterns. More than 40 predefined reports can be used as is or they can be customized, combining elements of other reports and saved for future use. Report generation can be automated to run on a scheduled basis and the results can be emailed or exported to PDF or Excel.
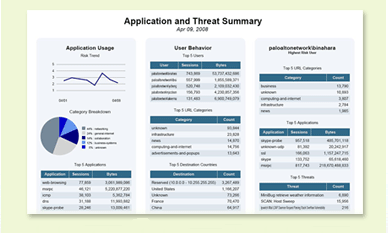
One-page summary report pulls data from any of the predefined or custom reports
to provide a holistic view of application, threat, and user activity.
The log viewer provides a view into application and threat activity with flexible filtering capabilities. Clicking on a cell value immediately creates a filter that can be narrowed down further by combining multiple criteria using an expression builder and additional log fields, even if they are not visible in the log viewer. The log viewer leverages the integration with directory services (Active Directory, LDAP, eDirectory), complementing application and threat views with user and group visibility. An export button is available to export any logs matching the current filter to a CSV file for offline archival or further analysis.
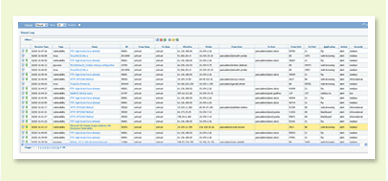
Quickly create advanced log filters to investigate traffic,
threat, configuration or system related incidents.
The trace session tool accelerates forensics or incident investigation with a centralized, correlated view across all of the logs for traffic, threats, URLs, and applications related to an individual session.
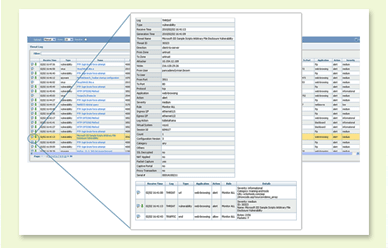
Trace session tool enables incident investigation with
a view of all logs for a particular session.
QoS & Real-time Bandwidth Monitor:
ACC provides administrators with immediate visibility into which applications are traversing the network, who is using them, and the potential security risk which in turn, enables a more informed policy control response.
Armed with these data points, administrators can apply QoS policies that ensure business-critical applications are not starved of bandwidth by non-work related applications.
- Guaranteed, maximum and priority bandwidth can be applied across 8 traffic queues.
- Policies can be applied to applications, users, source, destination, physical interface, IPSec VPN tunnel and more
- Diffserv marking is also supported, enabling application traffic to be controlled by a downstream or upstream device.









