Overview:
Global expansion, mobile workforces, and cloud computing are changing the ways organizations implement and deploy applications. Get the protection you need, where you need it, with Prisma™ Access. Prisma Access delivers a secure access service edge (SASE) that provides globally distributed networking and security to all your users and applications.
Whether at branch offices or on the go, your users connect to Prisma Access to safely access cloud and data center applications as well as the internet.
 What Makes Prisma Access Different?
What Makes Prisma Access Different?
Prisma Access is designed to prevent successful cyberattacks, and that’s why it does more than just secure the web. To stop cyberattacks, it’s necessary to inspect all traffic. Anything short of full inspection of all traffic introduces a significant gap in security.
Prisma Access consistently protects all traffic, on all ports and from all applications, enabling your organization to:
- Prevent successful cyberattacks with proven security philosophies and threat intelligence for deep visibility and precise control that extends across your organization.
- Fully inspect all application traffic bidirectionally—including SSL/TLS-encrypted traffic—on all ports, whether communicating with the internet, with the cloud, or between branches.
- Benefit from comprehensive threat intelligence powered by automated threat data from Palo Alto Networks and hundreds of third-party feeds.
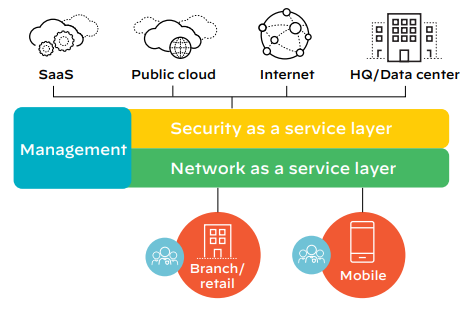
Network as a Service Layer
Prisma Access provides consistent, secure access to all applications—in the cloud, in your data center, or on the internet.
| Table 1: Secure Application Access Everywhere |
| Branch/Remote network |
|
|
|
|
|
|
|
| Mobile user |
|
|
|
|
|
|
|
Networking for Remote Networks
- Connect branch offices to Prisma Access over a standard IPsec VPN tunnel using common IPsec-compatible devices, such as your existing branch router, SD-WAN edge device, or a third-party firewall.
- Use Border Gateway Protocol (BGP) or static routes for routing from the branch.
- Use equal cost multi-path (ECMP) routing for faster performance and better redundancy across multiple links.
Networking for Mobile Users
- Connect mobile users with the GlobalProtect app, which supports user-based always-on, pre-logon always-on, and on-demand connections.
- Use an always-on full tunnel for optimal security. Prisma Access supports split tunneling based on access route, perapp VPN split tunneling, and split tunneling based on lowrisk/high-bandwidth applications, such as streaming video.
Bandwidth Management
- Enable application whitelisting and blocking policies with App-ID™ technology to free up the network from unnecessary, bandwidth-hogging applications.
- Prioritize and shape the traffic handled by Prisma Access using quality of service (QoS) policies.
Logging
- Take advantage of automated, centralized, cloud-scalable log storage.
- Centralize your management and reporting.
- Forward logs to your syslog server and/or security information and event management (SIEM) system.
Security as a Service Layer
Firewall as a Service
Prisma Access provides firewall as a service (FWaaS) that protects branch offices from threats while also providing the security services expected from a next-generation firewall. The full spectrum of FWaaS includes threat prevention, URL filtering, sandboxing, and more.
DNS Security
Prisma Access delivers our DNS Security service, which provides a combination of predictive analytics, machine learning, and automation to combat threats in DNS traffic. Organizations can block known malicious domains, predict new malicious domains, and stop DNS tunneling.
Threat Prevention
Using Prisma Access for threat prevention combines the proven technologies in the Palo Alto Networks platform, together with global sources of threat intelligence and automation, to stop previously known or unknown attacks.
Cloud Secure Web Gateway
Prisma Access for secure web gateway (SWG) functionality is designed to maintain visibility into all types of traffic while stopping evasions that can mask threats. Our web filtering capabilities also drive our credential theft prevention technology, which can stop corporate credentials from being sent to previously unknown sites.
Data Loss Prevention
Prisma Access combines integration with data loss prevention (DLP) controls that are API-driven (through Prisma SaaS) as well as in-line (through Prisma Access). These DLP policies allow organizations to categorize data and establish policies that prevent data loss.
Cloud Access Security Broker
Prisma Access and Prisma SaaS implement security controls that combine in-line security API security and contextual controls, acting as a cloud access security broker (CASB) to determine access to sensitive information. These controls are implemented in an integrated manner and applied throughout all cloud application policies.
Management
Prisma Access supports two management options:
- Panorama™ network security management for centralized administration across Palo Alto Networks Next-Generation Firewalls and Prisma Access.
- Cloud management through a web-based interface with preconfiguredprofiles and streamlined workflows,using the Prisma Access app in the hub.
At a Glance:
Prisma Access Highlights
- Protects remote networks and mobile users in a consistent manner, wherever they are.
- Provides connectivity and security to access all your applications.
- Offers flexibility and cloud scalability to handle your changing requirements.
Challenges Protecting Your Growing Organization
Cloud and mobility are driving changes in your network and your security requirements. To date, organizations have faced numerous challenges with implementing these changes on top of existing infrastructure:
- Backhauling traffic over virtual private network (VPN) connections or multiprotocol label switching (MPLS) circuits is inefficient and hurts the user experience.
- Routing branch and mobile user traffic directly to the internet without inspection is not safe.
- First-generation cloud-delivered security products, such as proxies, DNS filtering, and cloud access security brokers (CASB) have limited security capabilities.
These issues drive up administrative costs and create operational challenges, and the market demands a change. In 2019, Gartner defined a new cloud-delivered architecture for networking and security called the “secure access service edge” (SASE), which converges first-generation, standalone products with a common service delivery model.
Prisma Access
Prisma™ Access is a SASE that helps organizations embrace cloud and mobility by providing networking and network security services from the cloud. With a growing number of users, branch offices, data, and services located outside the protection of traditional network security appliances, organizations need a cloud-based infrastructure that converges networking and network security capabilities. Prisma Access provides consistent security services and access to cloud applications (including public cloud, private cloud, and software as a service), delivered through a common framework for a seamless user experience.
All users, whether at corporate headquarters, branch offices, or on the road, connect to Prisma Access to safely use cloud and data center applications as well as the internet. Prisma Access consistently inspects all traffic across all ports and provides bidirectional networking to enable branch-to-branch as well as branch-to-HQ traffic.
Prisma Access is delivered as a cloud service from more than 100 locations in 76 countries for users and branch offices to connect, enabling connectivity and security for mobile users, branch offices, and retail locations.
Prisma Access for Networks
Many branch offices and retail stores are geographically distributed and lack full-time IT staff, making deployment, management, change control, and hardware refreshes difficult.
Prisma Access can be used to connect remote networks over a standard IPsec connection—using any existing router, software-defined wide area networking (SD-WAN) edge device, or firewall that supports IPsec—to secure traffic, protect confidential information, and address data privacy needs. Prisma Access supports SD-WAN options using Palo Alto Networks Next-Generation Firewalls as well as third-party vendor products.
Prisma Access for Users
Mobile users need consistent security to access data center and cloud applications. Remote access VPN falls short because users typically connect to a gateway for access to data center applications, and then disconnect from the VPN to get better performance (but less security) when accessing cloud and internet applications.
Prisma Access brings protection closer to your users so traffic doesn’t have to backhaul to headquarters to reach the cloud. It works together with the GlobalProtect™ app on a user’s smartphone, tablet, or laptop. The app automatically establishes an IPsec/SSL VPN tunnel to Prisma Access for the enforcement of security policy without the backhaul to headquarters. With Prisma Access, all users have secure, fast access to all applications in the cloud, on the internet, or in your data center.
The GlobalProtect app also lets you establish access policies based on host information profile (HIP), enabling even more granular security policies tied to device characteristics—such as operating system, patch level, and the presence of required endpoint software—when accessing sensitive applications.
Large populations of users may need to change locations from time to time, as conferences, weather, and natural disasters can strain local infrastructure. Prisma Access monitors conditions and automatically scales to add capacity in regions that need it.
SASE Services
Prisma Access delivers both networking and security services, which include:
Networking
- SD-WAN—support for Palo Alto Networks Next-Generation Firewalls and integration with third-party SD-WAN
- VPN—options for connecting users and networks, including IPsec, SSL/IPsec, and clientless VPN
- Zero Trust network access (ZTNA)—access control and threat prevention to protect applications
- Quality of service (QoS)—prioritization of bandwidth for critical applications
- Clean Pipe—outbound internet security for managed service providers
Security
- Firewall as a service (FWaaS)—next-generation firewall security for branch offices and retail locations
- DNS Security—advanced analytics and machine learning to protect against threats in DNS traffic
- Threat Prevention—blocking of exploits, malware, and command-and-control (C2) traffic using threat intelligence
- Cloud secure web gateway (SWG)—blocking of malicious sites using static analysis and machine learning
- Data loss prevention (DLP)—categorize sensitive data and apply policies to control access
- Cloud access security broker (CASB)—governance and data classification to stop threats with in-line and API-based security
Licensing Options
Prisma Access for Networks is licensed based on the total bandwidth used across all sites, with the bandwidth pool divided into the amounts each location needs (minimum bandwidth pool: 200 Mbps).
Prisma Access for Users is licensed based on the total number of users, with tiers from 200 users up to more than 100,000. Prisma Access for users requires the GlobalProtect app. Supported endpoints include Microsoft Windows®, Apple macOS® and iOS, Android®, Google Chrome® OS, and Linux.
Technical Specifications:
| Prisma Access Details, Features, and Specifications |
| Use cases |
- Branch offices/retail
- Virtual private clouds
- Palo Alto Networks SD-WAN hub
- Third-party SD-WAN security
|
- Mobile users with:
- Laptops
- Smartphones
- Tablets
- Zero Trust network access
|
- Service provider/telco multitenant environments
- Security of traffic outbound to the internet
|
| Basis |
Based on bandwidth pool; each connection can be assigned up to 300 Mbps (500 Mbps and 1 Gbps currently available in preview) |
Based on total number of unique users |
Based on bandwidth pool; can be divided up to 10 Gbps per tenant |
| Minimum deployment size |
Bandwidth pool of 200 Mbps |
200 users |
100 Mbps per tenant |
| Baseline service tunnels |
Up to three service tunnels included |
N/A |
| Additional service tunnels |
Additional service tunnels (up to a total of 100) can be created by allocating 300 Mbps of the bandwidth pool per additional tunnel |
N/A |
| Locations |
100+ in 76 countries |
17 locations |
| Connection type |
IPsec tunnel SD-WAN (PAN-OS 9.1 or later) |
GlobalProtect app IPsec/SSL |
Peering via Partner Interconnect (VLAN attachment per tenant) |
| GlobalProtect app platform support |
N/A |
Apple iOS
Apple macOS
Google Android
Google Chrome OS
Linux CentOS
Red Hat Enterprise
Linux
Ubuntu
Windows 7, 8, 10, and UWP |
N/A |
| Panorama |
- License for Panorama required
- No license for Prisma Access Panorama plugin
- Prisma Access does not count against the Panorama device license
|
| Cloud management |
No license required for Prisma Access app on the hub |
| URL Filtering |
Included |
| Threat Prevention |
Included |
| WildFire |
Included |
| Host information profile |
Included |
| DNS Security |
Included |
| Data loss prevention |
Subscription required |
| Cortex XDR |
Subscription required |
| Prisma SaaS |
Subscription required |
| AutoFocus |
Subscription required |
| Cortex Data Lake |
Prisma Access requires Cortex Data Lake for logging (subscription required) |


 What Makes Prisma Access Different?
What Makes Prisma Access Different?